IOS逆向安全(5)-实战绕过双向认证
0x01 ios抓包配置
(1)Burpsuite代理配置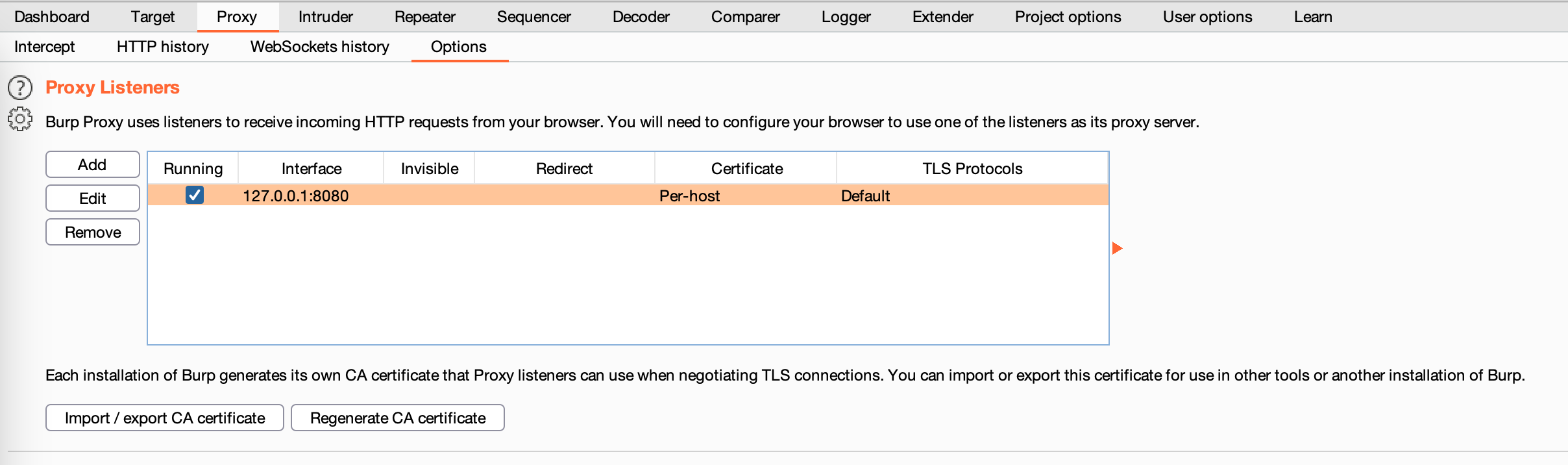
(2)ios手机代理配置
(3)访问http://burp 下载证书
手机描述文件点击验证
(4)证书勾选信任
0x02 测试app
(1)网络不给力
其他APP都正常,只有这个APP提示网络有问题
猜测有防御措施
(2)脱壳
使用DumpDecrypter进行脱壳,如下
改后缀,解压
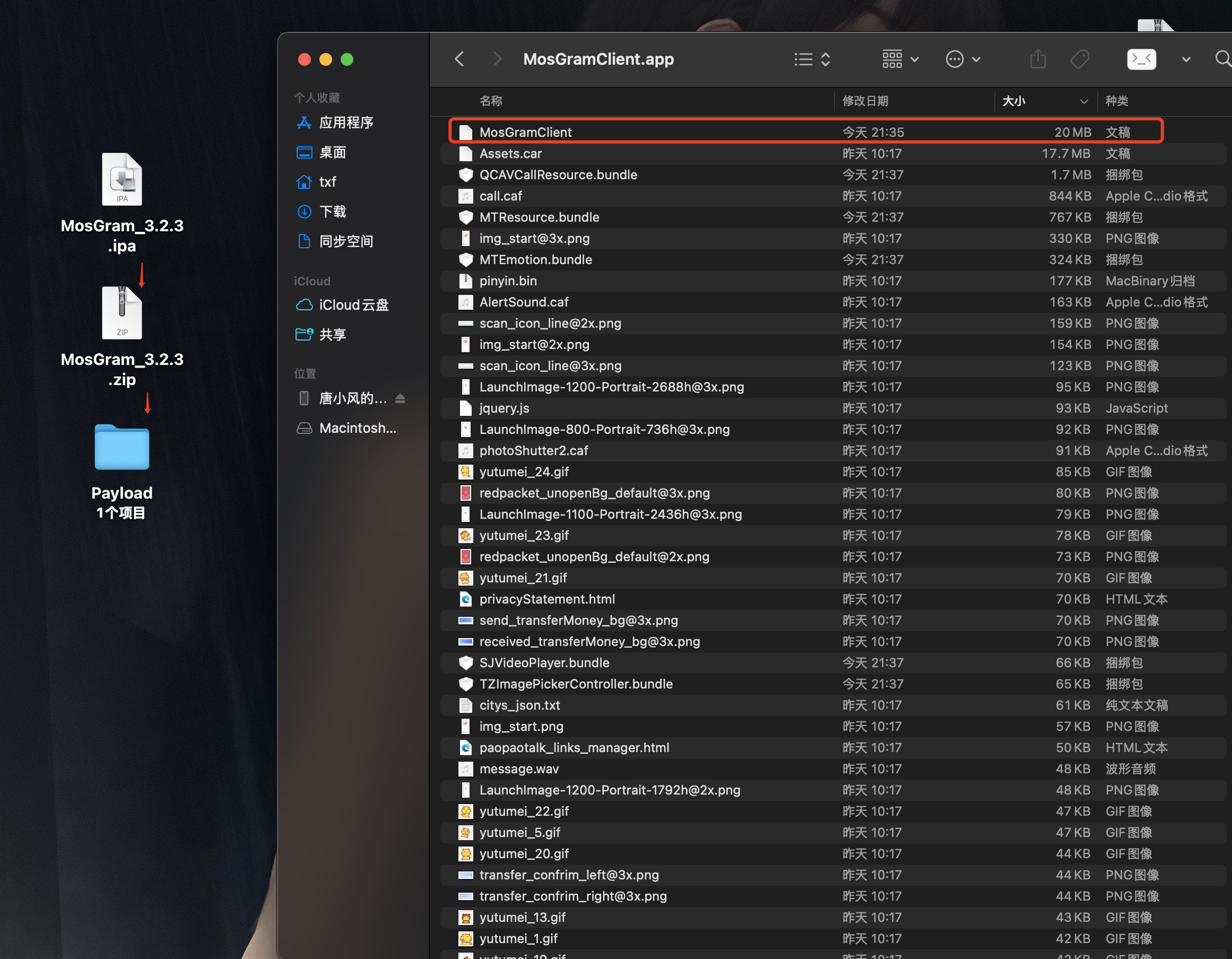
找到app包内的证书
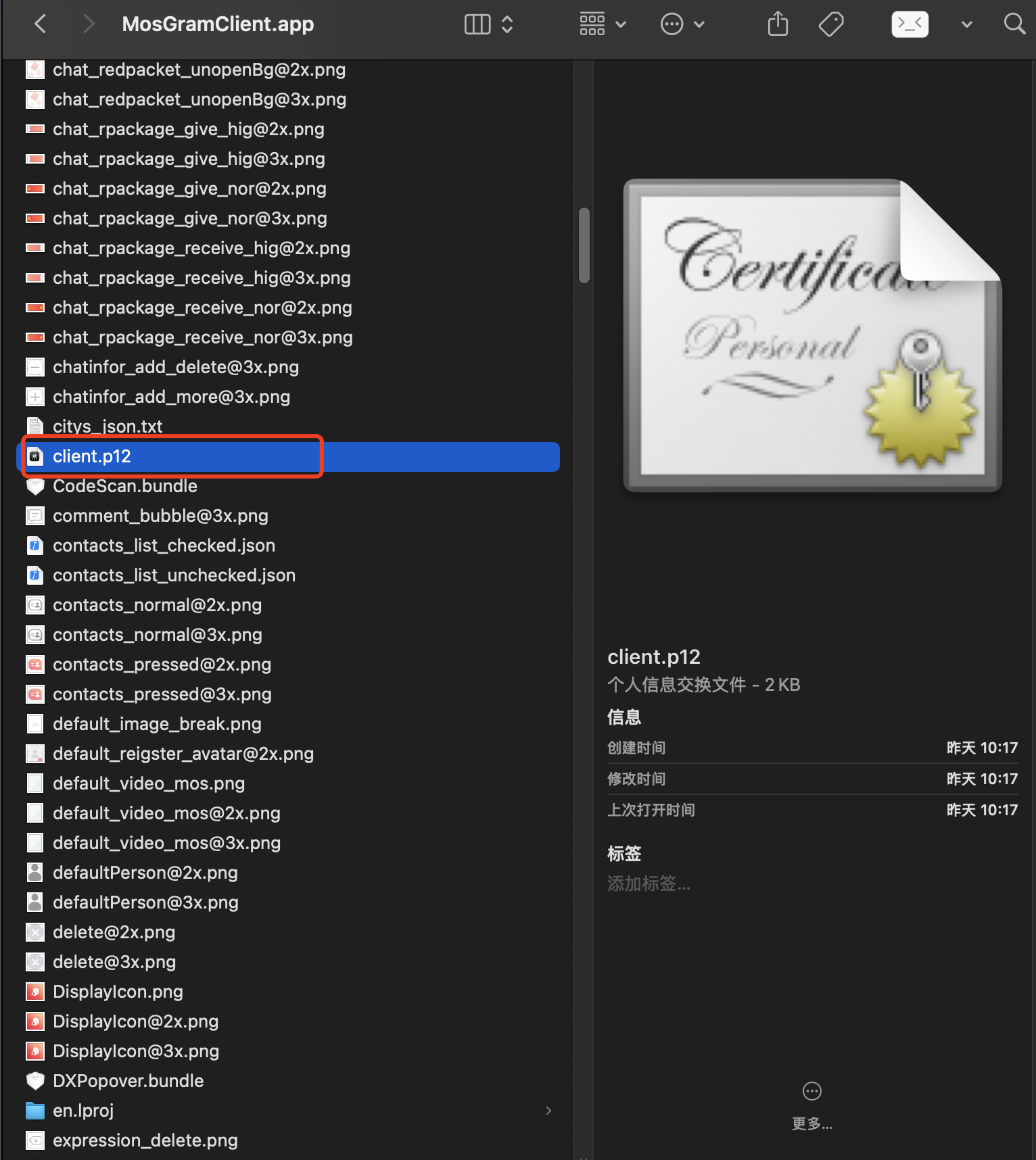
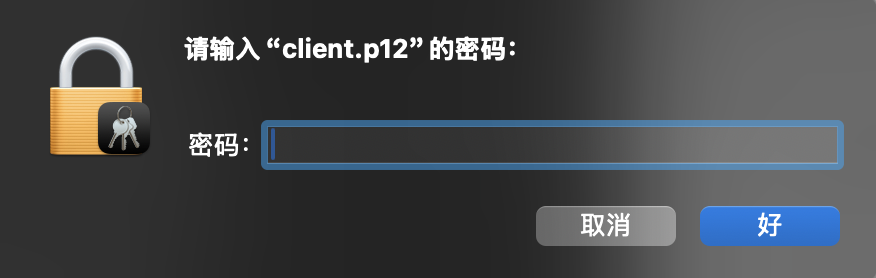
(3)HOOK
APP肯定会读取证书,所以先尝试hook读取证书的行为
frida-trace -UF -m "*[NSBundle pathForResource*]"点击登陆,确认存在调用
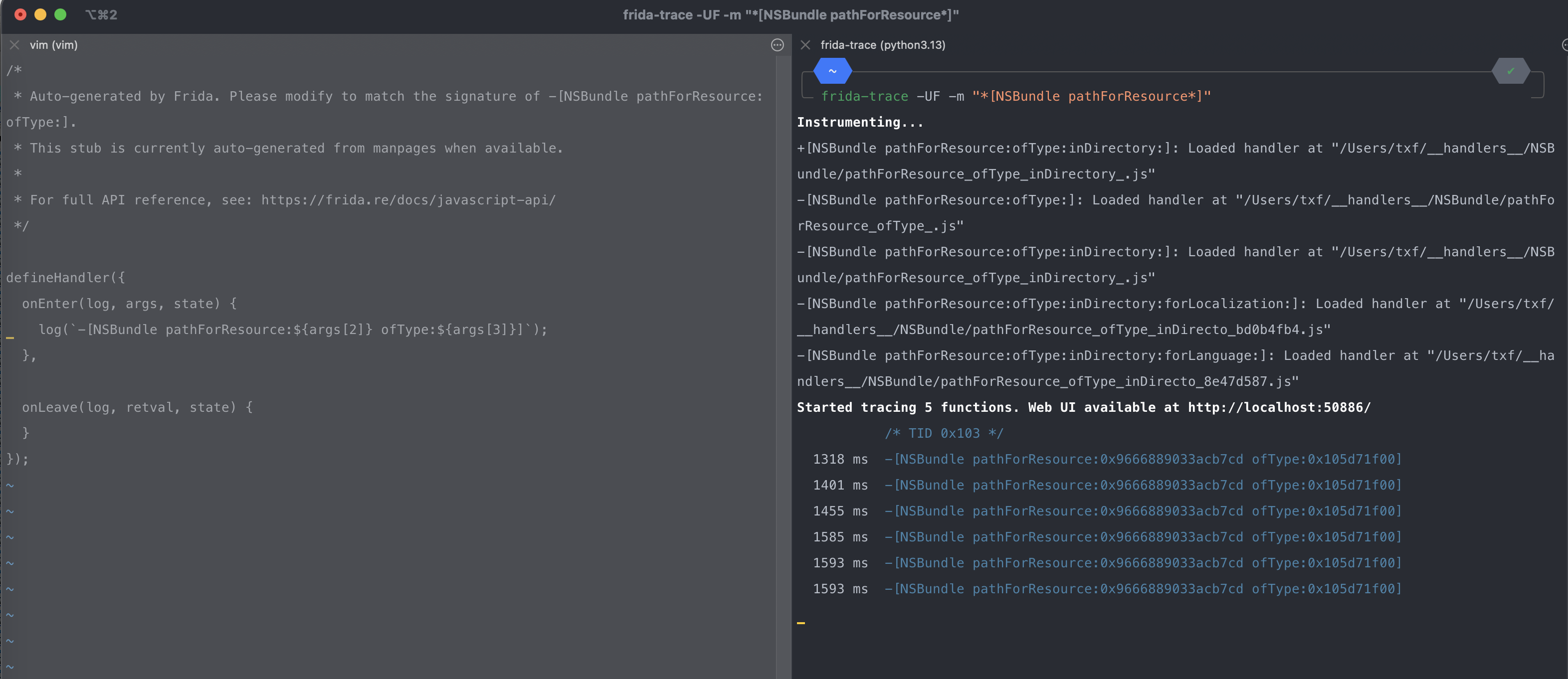
对/Users/txf/__handlers__/NSBundle/pathForResource_ofType_.js进行修改
修改前:
/*
* Auto-generated by Frida. Please modify to match the signature of -[NSBundle pathForResource:ofType:].
* This stub is currently auto-generated from manpages when available.
*
* For full API reference, see: https://frida.re/docs/javascript-api/
*/
defineHandler({
onEnter(log, args, state) {
log(`-[NSBundle pathForResource:${args[2]} ofType:${args[3]}]`);
},
onLeave(log, retval, state) {
}
});修改后:
defineHandler({
onEnter(log, args, state) {
console.log('NSBundle pathForResource called from :\n' +
Thread.backtrace(this.context, Backtracer.ACCURATE).map(DebugSymbol.fromAddress).join('\n')
);
log(`-[NSBundle pathForResource:${ObjC.Object(args[2]).toString()} ofType:${ObjC.Object(args[3]).toString()}]`);
},
onLeave(log, retval, state) {
}
});再次Hook
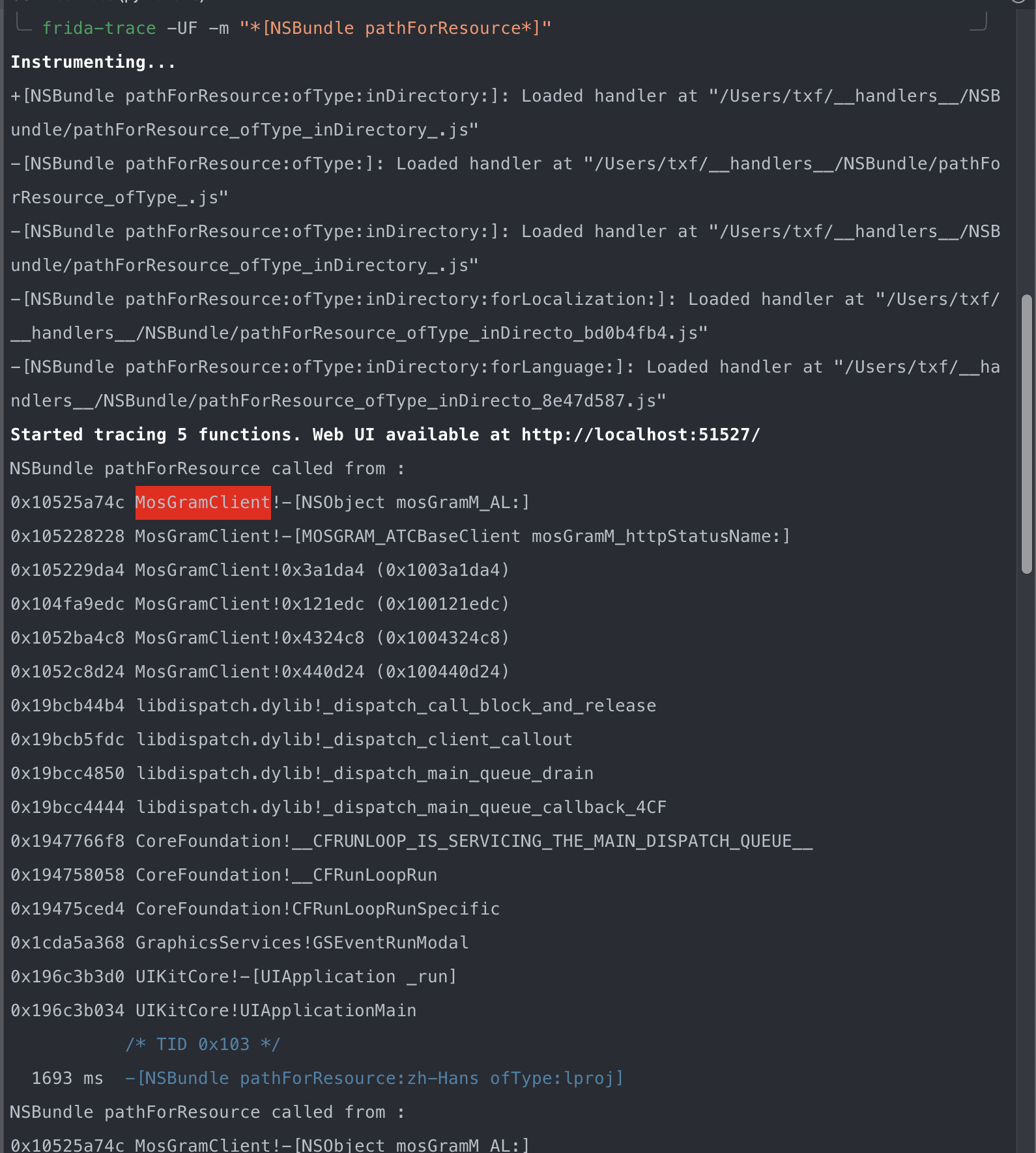
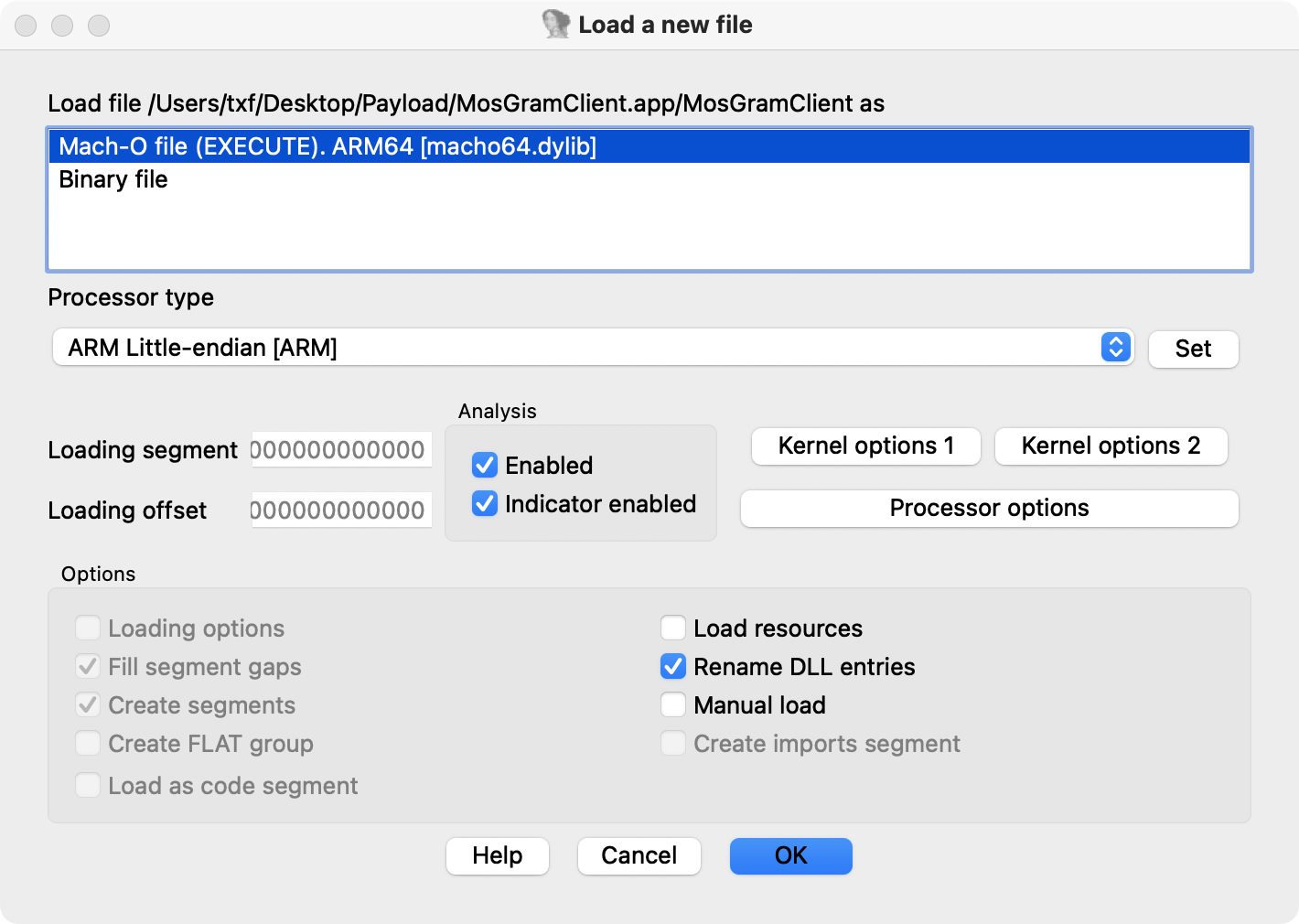
寻找0x1003a1da4 进行逆向
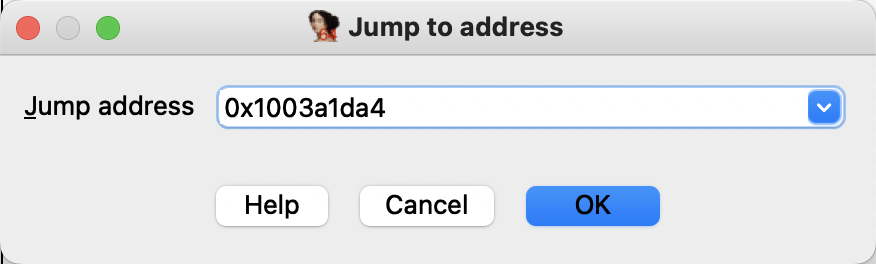
按g进行地址跳转
F5对代码转换
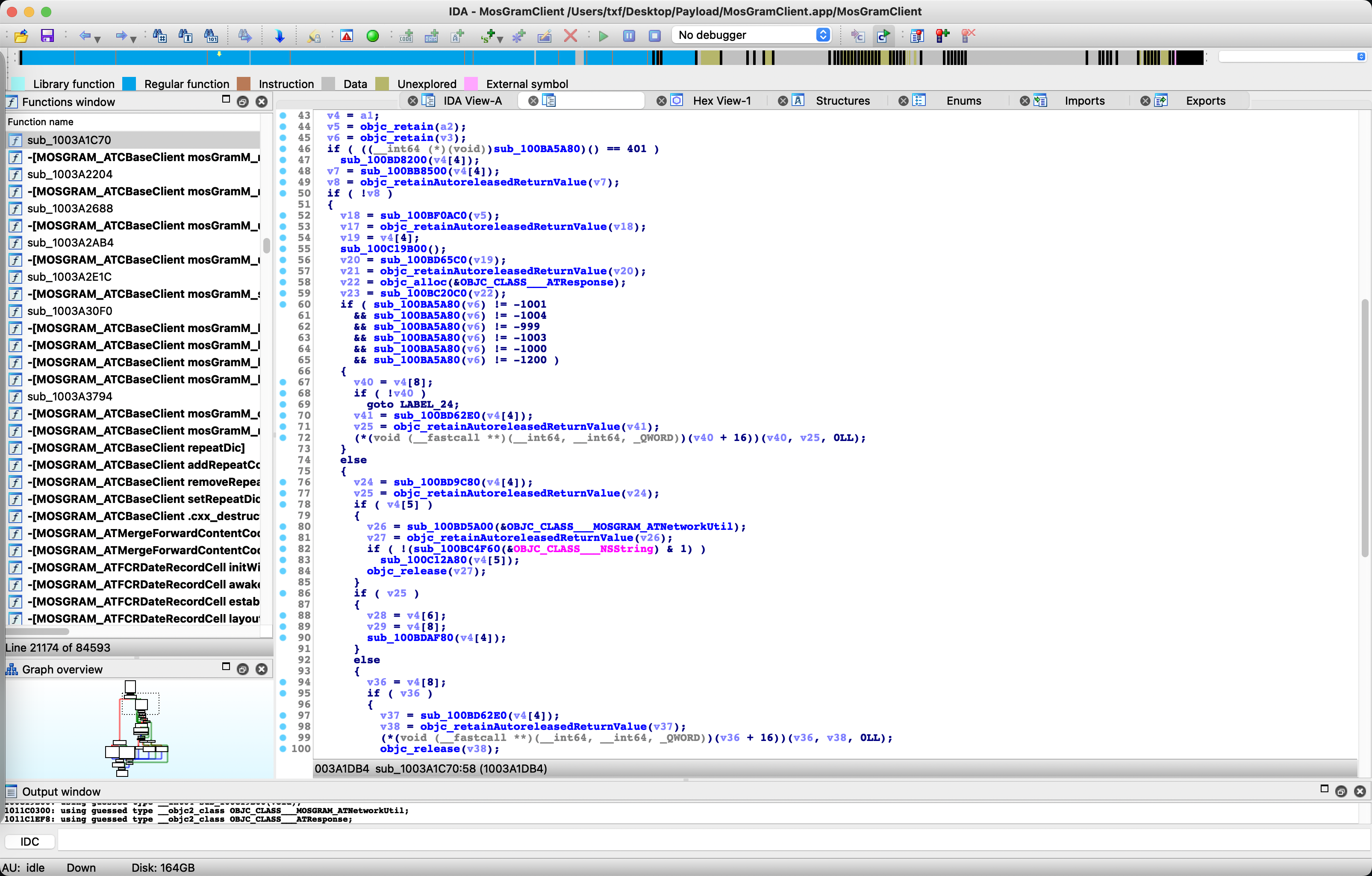
定位到:
v20 = sub_100BD65C0(v19);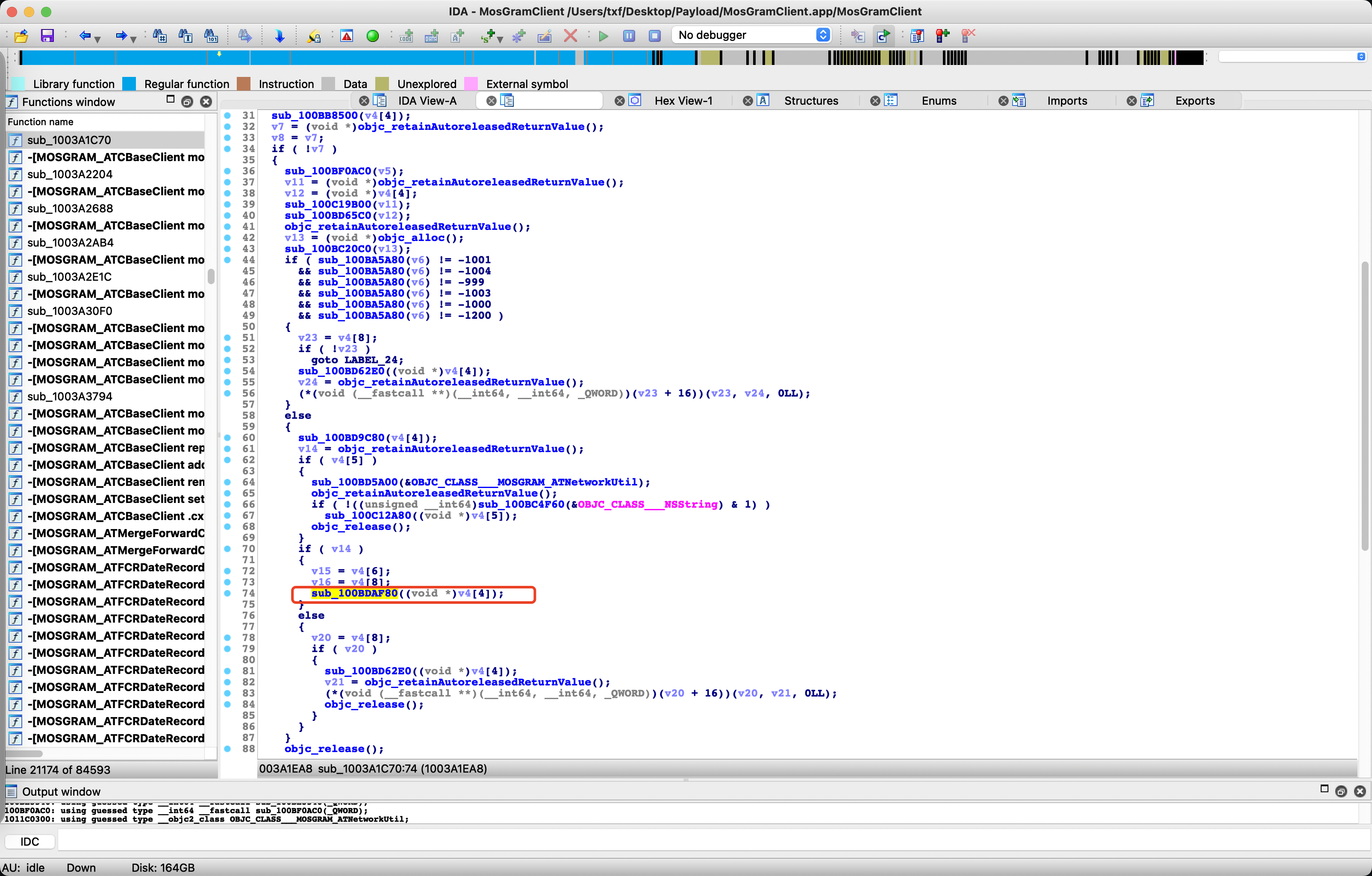
跳到
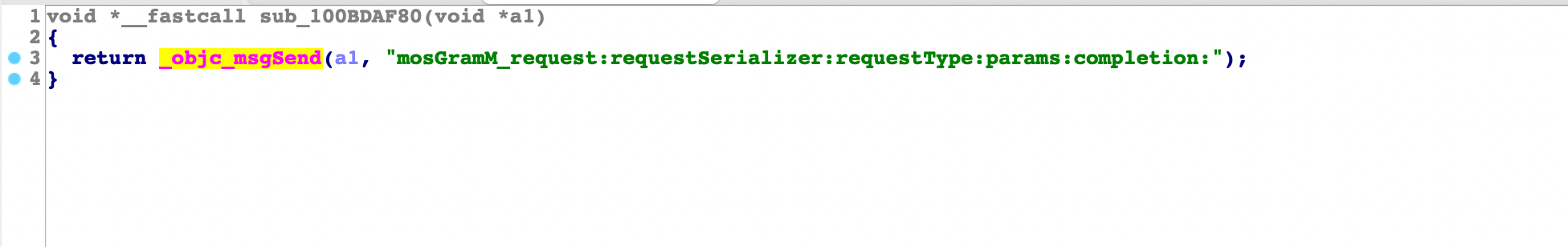
查找方法 mosGramM_extractIdentity:toIdentity:]
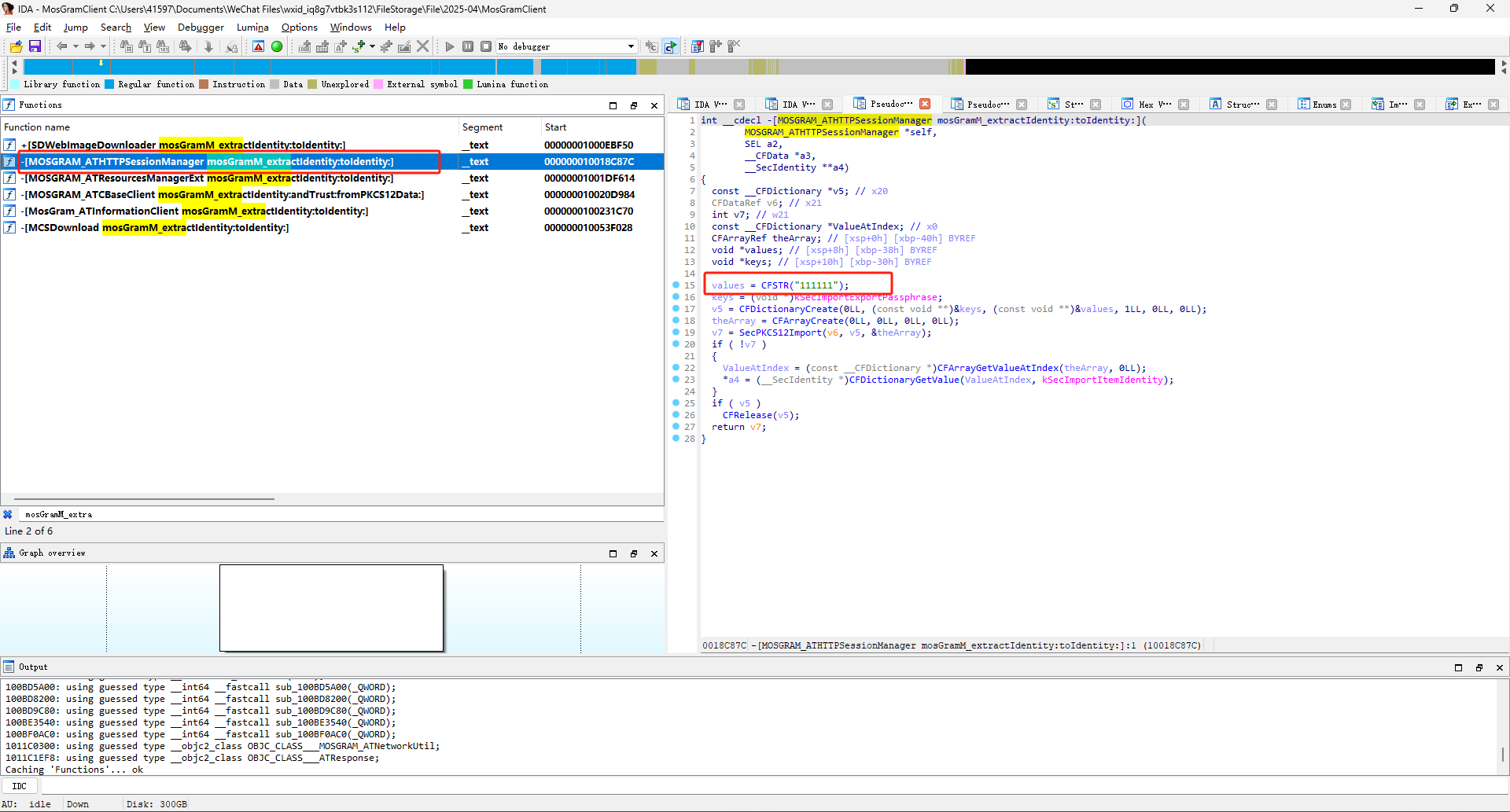
密码 "111111"
License:
杭州小单纯